Seattle, WA - The engineering floor at Nimbus Cloud was briefly hopeful Tuesday morning when the CISO announced a new “Shift Left” initiative, describing it as “a company-wide commitment to getting leaner, stronger, and more secure.”
“I thought we were finally getting gym memberships,” said DevOps lead Aaron Patel, wiping down his standing desk. “Then he pulled up a PowerPoint with attack chains instead of workout plans. I was already halfway into a plank.”
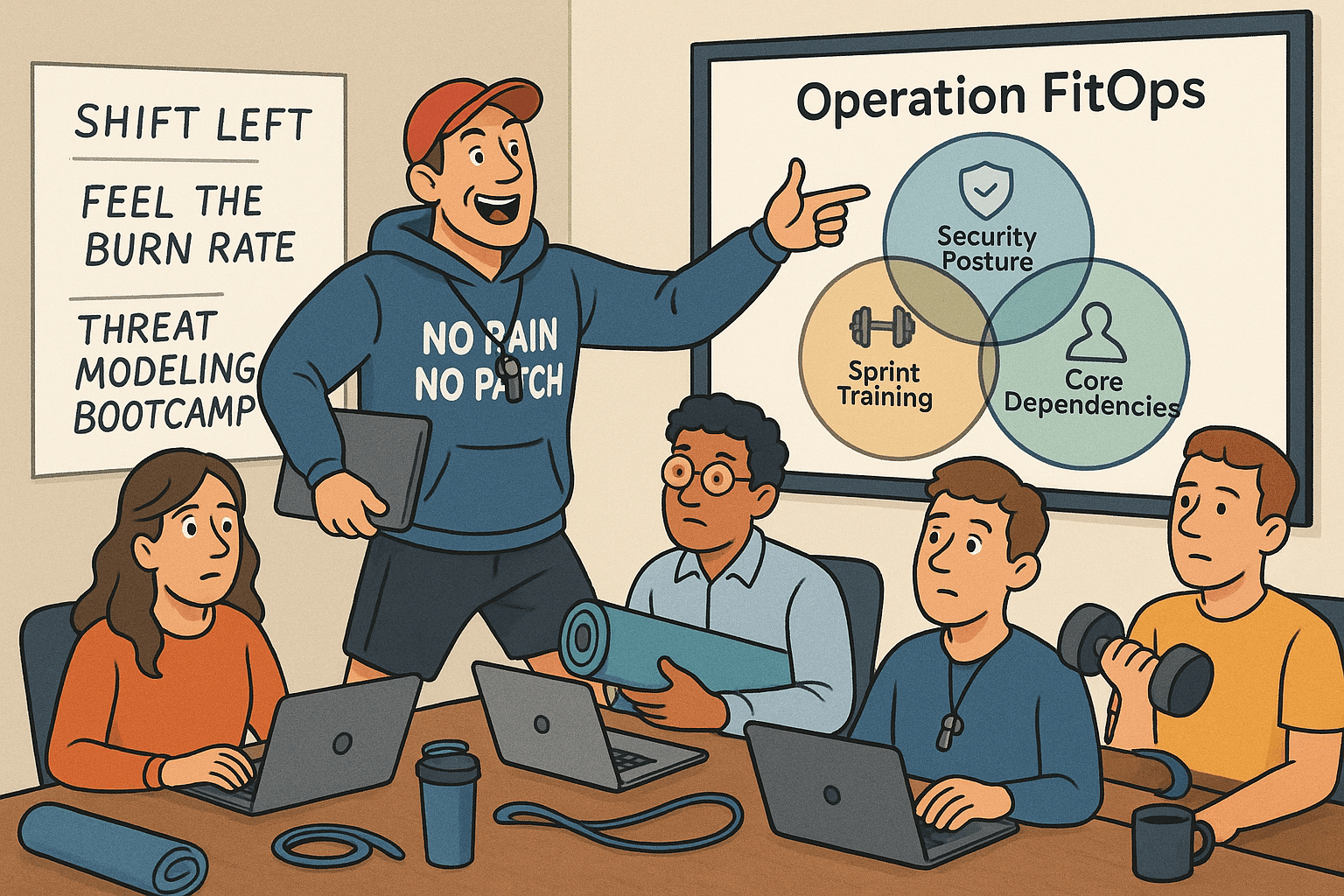
The new program, internally branded Operation FitOps, aims to integrate security earlier in the development process. Unfortunately, no one agrees on what “earlier” actually means.
Security insists it starts before code exists.
Engineering insists it starts after coffee exists.
The Fitness Analogy Gets Out of Hand
The CISO, Greg Baxter, reportedly kicked off the announcement wearing a branded hoodie that read ‘No Pain, No Patch.’
In his presentation, he compared code review to “core work,” penetration testing to “cardio,” and compliance audits to “detox.”
He then challenged developers to “sweat out technical debt” before the end of Q3.
“He had a whistle,” said frontend engineer Dana Cho, visibly shaken. “He kept yelling, ‘Feel the burn rate!’”
Following the announcement, all development pipelines were paused for a “warm-up sprint,” which consisted of deleting old Jenkins jobs and labeling it “mobility work.”
When Metrics Become Calories
Internal documents obtained by The Exploit reveal that the Shift Left strategy was inspired by a Gartner white paper titled ‘Security Posture as a Lifestyle Choice.’
The plan replaces traditional metrics like CVSS scores and MTTR with new “health indicators,” including:
Resting Risk Rate (RRR): The number of unpatched vulnerabilities per engineer at rest.
Patch Pressure Index (PPI): How close a developer is to rage-quitting during a compliance review.
Threat Burn Ratio (TBR): Vulnerabilities closed divided by calories consumed during incident response.
“We want security baked in, not bolted on,” said Baxter. “Or maybe grilled - whatever’s lower-fat.”
Engineers Protest ‘Mandatory Yoga for Pipelines’
Within 24 hours, engineers began reporting side effects of the new regime, including “context fatigue,” “compliance cramps,” and one documented case of “GitHub burnout.”
“He told us to stretch our sprints,” said SRE manager Jason Liu. “We told him velocity doesn’t work like that. Then he printed out a burndown chart and called it a calorie tracker.”
To encourage participation, Security introduced Threat Yoga Thursdays, during which developers must remediate one vulnerability per deep breath. Participation rates dropped to zero after the first session, when a senior backend engineer attempted to achieve “Zen patching” by deleting the entire staging environment.
AI Personal Trainer Enters the Chat
In an attempt to modernize the initiative, Nimbus deployed AI-SecCoach, an LLM-based assistant that automatically comments on pull requests with “motivational security feedback.”
Within hours, the bot was flagging TODO comments as “self-doubt indicators” and suggesting encryption for emotionally sensitive code.
“It told me my test coverage looked ‘sluggish,’” said QA engineer Priya Singh.
“Then it refused to merge my PR until I promised to believe in myself.”
AI-SecCoach has since been promoted to Head of Culture after successfully gaslighting the entire company into believing security debt is a mindset.
In Closing
At press time, the CISO was seen leading a group of engineers through a “threat modeling bootcamp,” shouting phrases like “tighten those dependencies!” and “no excuses, only exploits!”
Morale remains mixed.
Some engineers claim they’ve learned to appreciate the discipline of early security reviews. Others have joined a stealth Slack group called #ShiftRightBack, dedicated to “reclaiming our weekends.”
“I get what he was trying to do,” said one senior developer, staring into the distance. “We all want to be stronger. We just didn’t think it meant core training for our pipelines.”
Security has already declared the initiative a success, citing a 200% increase in “awareness,” 0% increase in actual fixes, and a company-wide drop in carbohydrates.
About the Author

Subscribe before we're patched
Like a vitamin you ingest with your eyes. The best cybersecurity parody, delivered.